What Is Vulnerability Management and Why Do So Many Companies Get It Wrong?

Vulnerabilities are typically defined as gaps in the security of networks, systems, and applications. We all know that it’s critical to address them before these weaknesses can be exploited to gain unauthorized access, disrupt services, or steal data.
So when it comes to vulnerability management, how and why do so many companies seem to get it wrong?
What is Vulnerability Management?
First of all, let’s make sure we’re all on the same page about what exactly this security practice entails.
Vulnerability management is an ongoing effort intended to identify, prioritize, and remediate weaknesses in software and systems across your entire organization. Most businesses have scanning processes in place, but a comprehensive vulnerability management program should be so much more than that. (Don’t worry, we have the numbers to prove it).
A true vulnerability management program is hand-tailored to the organization and should focus on risk-based asset management, process structure, exposure awareness, vulnerability prioritization, and of course, remediation.
What Companies Get Wrong About Vulnerability Management
A vulnerability management program is not really a vulnerability management program if:
- You’re just scanning and patching, or you aren’t scanning and patching all that often.
- You’re not also participating in ongoing asset management – you can’t scan and patch what you don’t know you have!
- You aren’t contextualizing the level of risk associated with uncovered vulnerabilities and weighing that against the effort to remediate. If remediation efforts are mis-prioritized, you could be stuck addressing less consequential vulnerabilities before remediating more important issues.
- You aren’t communicating vulnerability management initiatives, progress, and risk levels to leadership.
- You don’t repeat the cycle of vulnerability management continually throughout the year. Threats and vulnerabilities don’t only pop up quarterly or annually.
So, are you scanning often enough? Are you patching often enough? Or do you have ‘doors and windows’ left open between vulnerability management efforts?

Here’s the good news: In our first annual InfoSec report published last year after analyzing over 400 validated security assessments from 2022, we found that most organizations had no critical or high-severity vulnerabilities on externally accessible systems.
86% of organizations had no critical severity (CVSS 10) vulnerabilities on systems exposed to the internet.
82% had no high-severity (CVSS 7-9) vulnerabilities on systems exposed to the internet.
The bad news is that 14-18% still did.
Why is this? Last year’s findings around scanning frequency and vulnerability management may begin to paint a picture.
32% of all ransomware and internal compromise cases and 24% of all cases in general were the result of a vulnerability being exploited.
Another key finding: just one vulnerability exploit was the result of a vulnerability published in the last 12 months. All others had been published the previous year or before. One even dated back to 2017.
As far as frequency and cadences go, the numbers are a little more encouraging. About half of the 400 companies we assessed met our minimum standards for scanning, validation, and timeline organization.
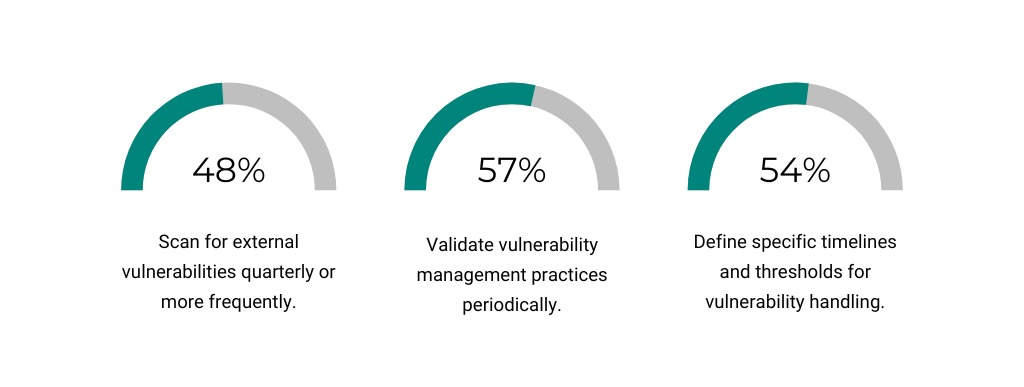
One thing that just doesn’t sit right with us, is that most of these results are from assessments performed for SMBs–businesses that often cannot afford to suffer a security incident let alone a full-blown ransomware event. But it’s a double-edged sword because smaller companies can’t always afford to hire a robust in-house IT and security team either.
Security professionals and IT experts with the knowledge to properly secure your business, do not come cheap. We get it.
So let’s talk about what a proper vulnerability management system should look like, and see how well your company’s protocol stacks up to our recommendations.
FRSecure’s Approach to Vulnerability Management
FRSecure’s analyst team works with our clients to implement a cyclical six-step vulnerability management system that spans from planning to scanning to prioritization and remediation, reporting, and of course–circling back to validate our efforts and start the process all over again.
Let’s touch on each of these steps in a little more detail.
Plan
Determining the scope of the vulnerability management program is an important step in ensuring efforts and resources are focused effectively. We look at things like assets, network segmentation, third-party systems, and regulatory requirements to choose how to tackle risks.
Scan
Scanning is likely the most recognizable and already-enacted component of vulnerability management across organizations. We’ll work with you on asset discovery, vulnerability assessments, and formulating a recommended schedule.
Report & Prioritize
This is where we work with you to determine what vulnerabilities and systems should be remediated in what order. This is always done with the risk posed to the organization top of mind, and is informed by vulnerability and asset risk ratings.
Act
Identifying vulnerabilities through scans means nothing if we don’t do something about them! In the action phase, the response is prescribed. This is typically focused on remediation—fixing identified vulnerabilities. In scanning, this is often (but not limited to) patch management.
Validate
It’s not enough to simply patch and remediate our vulnerabilities. We need to ensure that the changes made were successful. Our team always works with clients to re-scan and validate the effectiveness of our changes after the fact.
Reassess & Enhance
It is important to regularly review and reassess the scope of your vulnerability management program to ensure it remains aligned with your organization’s evolving infrastructure, technology landscape, and security priorities. We’ll now start the cycle again from step one with these things, and all of our learnings from the previous scan in mind!
How to Create a Vulnerability Management Program With Limited Resources
So, we now know that simply scanning and patching isn’t enough for a robust vulnerability management program. But how can you create a system that effectively protects your organization, especially if you’re a smaller business with limited resources?
Here are some key takeaways to keep in mind:
- Prioritize Based on Risk: Not all vulnerabilities are created equal. Focus on patching critical vulnerabilities that pose the biggest threat to your business first. The CVSS (Common Vulnerability Scoring System) is a good place to start assigning weight to those vulnerabilities.
- Automate Where Possible: There are many affordable vulnerability scanning tools available that can automate at least a portion of the process. This frees up your IT team to focus on more complex tasks.
- Patch Management is Key: Having a system in place to deploy patches quickly and efficiently is essential. Many software vendors offer automated patching solutions.
- Start with Free and Open-Source Tools: There are a number of free vulnerability scanners available that can identify basic security weaknesses.
- Focus on Critical Assets: Identify the systems and data that are most critical to your business operations and focus your vulnerability management efforts there.
- Conduct Regular Reviews: Schedule regular scans and security assessments, even if they can’t be done daily or weekly.
- Prioritize Patching: Develop a plan for deploying critical patches as soon as they become available.
Wrapping Up
Remember, vulnerability management is an ongoing process, and it will always require some level of time and resource investment to get right. But it’s time well spent.
As we discussed earlier, 14-18% of companies have high-severity or critical vulnerabilities on systems accessible via the internet, and nearly 25% of all ransomware and internal compromise cases were the result of a vulnerability exploit more than a year old. Do not let this part of your security program fall through the cracks.
By continuously identifying, prioritizing, and remediating vulnerabilities, you can significantly reduce your risk of a security incident over time.
Need help with anything we covered in this article? Feel free to send us your questions and we’ll be more than happy to help in any way we can.
