NIST CSF 2.0: Highlights In The Recent Update

On August 8, 2023, NIST published the initial public draft for version 2.0 of its Cybersecurity Framework (NIST CSF 2.0). It’s the first update since version 1.1 was released back in 2014, and this was due and needed. Below we will assess the changes to the framework, discuss the updates, and highlight the differences 2.0 brings from 1.1.
About NIST CSF
NIST is the National Institute of Standards and Technology—this organization was created to foster technological and industrial advancement—and to set standards for science and technology.
NIST’s cybersecurity framework is the CSF, first developed in 2004, this framework created standards, guidelines, and best practices to help businesses and organizations manage their cybersecurity risk.
Broad adoption of NIST
It’s important to realize that NIST is not a regulatory body and its CSF is not a regulatory requirement. That said, it is a requirement for government agencies, however. Frequently companies who work with those agencies are often required to comply as a result.
And the CSF is fairly broadly adopted – nearly half of all U.S. organizations had adopted NIST CSF by 2020.
As a result, it’s been widely accepted as an industry standard framework in the information security space.
Controls Contained In NIST CSF
In the most recent version of NIST CSF, there are 23 categories of controls, which span five function areas:
- Identify
- Protect
- Detect
- Respond
- Recover
Within the above categories, there are 108 subcategories.
Key Differences Between NIST CSF 1.1 and NIST CSF 2.0
We’re only about a month from the release of the draft of NIST CSF 2.0. And given that the draft will not be open to comments until November 5, what is reviewed here may not reflect the final release. However, I expect it to be close, and this at least allows organizations to become familiar with it before its official launch.
NIST CSF 2.0 Be Release Timetable
The current plan is to publish the final version of NIST CSF 2.0 in early 2024.
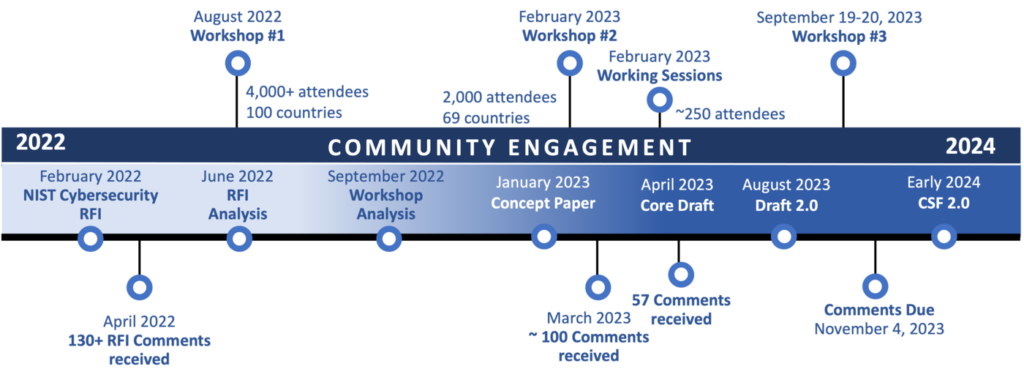
NIST CSF 2.0 Updates – Highlights
Govern Function
The enhancement here is a sixth function – Govern – that sits occupies the center of the diagram, placed there to guide organizations about how to implement the other five functions.
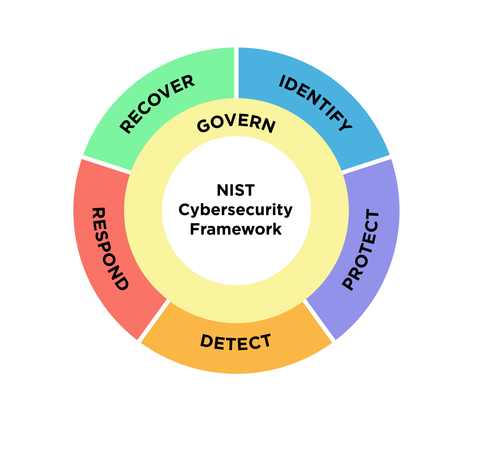
A New Name For The Framework
The second major enhancement is to rename it from “Framework for Improving Critical Infrastructure Cybersecurity” to “Cybersecurity Framework.” The scope changed to critical infrastructure, as it was known under 1.1, to reflect the broad use across all organizations.
Impact Of The Changes
The main change is a realignment and better segmentation of controls. The original five functions included governance of each those functions, and controls will be integrated into this new function.
Not surprisingly, NIST rewrote the subcategories, primarily so they are more understandable to the public, and we fully expect to see new proposed subcategories under the Govern function.
NIST CSF 2.0 Realignment – Govern Function
An example of the realignment is below, and makes perfect sense for the Govern function – its use in a supply chain risk management context is a more natural fit as a govern function than an identify function:
- Supply Chain Risk Management (ID.SC): Dropped (moved to GV.SC)
- ID.SC-01: Dropped (moved to GV.SC-01)
- ID.SC-02: Dropped (moved to GV.SC-03, GV.SC-07)
- ID.SC-03: Dropped (moved to GV.SC-05)
- ID.SC-04: Dropped (moved to GV.SC-07)
- ID.SC-05: Dropped (moved to GV.SC-08, ID.IM-02)
NIST describes the objective of this new function as to “establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy.”
It’s nice to see the function define the requirements for executive leadership and stakeholder expectations – it’s essentially stating that to have a successful cybersecurity program, you need to have buy-in and support across the highest levels of the organization.
It is clear from the categories within Govern that NIST is stating cybersecurity as an organizational risk and cannot simply be an afterthought.
| Function | Category | Category Identifier |
| Govern (GV) | Organizational Context | GV.OC |
| Risk Management Strategy | GV.RM | |
| Cybersecurity Supply Chain Risk Management | GV.SC | |
| Roles, Responsibilities, and Authorities | GV.RR | |
| Policies, Processes, and Procedures | GV.PO | |
| Oversight | GV.OV |
It’s also reassuring to see there are a number of new controls in Govern such as:
- GV.OC-02: Internal and external stakeholders are determined, and their needs and expectations regarding cybersecurity risk management are understood.
- GV.RM-05: Lines of communication across the organization are established for cybersecurity risks, including risks from suppliers and other third parties.
These make it undeniably clear that cybersecurity is an enterprise-wide program for organizations.
NIST CSF 2.0 Category Modifications
A select set of categories were ] renamed in NIST CSF 2.0 to better communicate their intent. While others were either reorganized and removed altogether. For example, Information Protection Processes and Procedures (PR.IP) are not to be found in the NIST CSF 2.0 draft—all its subcategories were sensibly placed in other categories, creating better alignment.
While it will be important to understand where they have been placed, and if an organization is following CSF 1.1, the control is still availabe.
Platform Security (PR.PS) and Technology Infrastructure Resilience (PR.IR) are relevant examples of new categories that better represent today’s cybersecurity environment, and include a combination of existing subcategories that were moved and entirely new subcategories as well. The rewording of controls leaves the spirit intact, and now focused on an active program.
ID.AM 1 and ID.AM2 are great examples of this.
| Subcategory | V1.1 | V2.0 Draft |
| ID.AM1 | Physical devices and systems within the organization are inventoried | Inventories of hardware managed by the organization are maintained |
| ID.AM2 | Software platforms and applications within the organization are inventoried | Inventories of software, services, and systems managed by the organization are maintained |
This proactive approach is consistent throughout 2.0 and will ensure organizations are vigilant about embracing change rather than performing an initial assessment and letting it become out of date and inaccurate. Too frequently organizations will declare “Yes we have an asset inventory” only to realize it has never been updated.
Every organization knows that the only constant in information security is change, and that reality should guide governance and controls.
If an organization is not proactive—continually working on their security integrity—they run the risk of putting themselves at even higher risk.
Final Remarks
Overall, there is not a lot of change here. CSF 1.1 strengthened 22 categories and 108 subcategories. CSF 2.0 represents 23 categories and 106 subcategories – and with the exception of the increased emphasis on comprehension, governance, and stakeholder obligations, the core concepts remain the same.
But knowing change is the only constant organizations deal with, the best way to remain ahead of changes is to build a security-first culture. And that is most effectively and durably done from the top down, within every department of an organization.
Mirrored Defense makes this easy to get started – get a get a free surface area scan today to assess your risk, and identify paths to remediation. Take a meaningful step towards making cybersecurity more understandable.
