Cloud Cyber Security Mistakes and How to Avoid Them

There’s no question about it: cloud computing offers a lot of value to modern businesses.
Unprecedented flexibility, unlimited scalability, and never-before-seen collaborative capabilities are just a few. However, despite strategically worded marketing materials from many providers, these solutions are not inherently more secure than their on-premise counterparts.
It is a common misconception across all kinds of industries: moving to the cloud alone does not make your data more secure.
Like so many other recent tech advancements, cloud computing is both an incredible advancement and yet another attack surface for threat actors to exploit.
With this in mind, let’s discuss some common cloud cyber security mistakes and how to avoid them. But first, let’s dive into the basics and make sure we’re all on the same page here.
What is Cloud Security?
Cloud security is concerned with the set of technological controls designed to protect data, applications, and infrastructure within cloud computing environments.
The objective here is exactly the same as the on-premise concepts we’ve discussed in the past—to ensure confidentiality, data integrity, and availability while mitigating risks like unauthorized access, data breaches, and downtime.
How Secure is the Cloud?
Cloud services can be a great tool for businesses, but are only as secure as the business accessing them.
While cloud service providers invest heavily in security measures, the ultimate security responsibility lies with the user. Adopting best practices, configuring security settings, and monitoring for anomalies are essential for a secure environment.
We’re going to stress the importance of properly configuring your cloud environment and access protocol a lot in this article, but it should be said that it is also possible for a cloud environment to be better protected overall than your on-premise infrastructure.
Cloud environments are encrypted, backed up regularly, and often have built-in threat monitoring.
While we can report that most organizations have an effective backup strategy, and most have an off-site storage procedure in place, many still have network connectivity to the backup location.
- 91% of organizations have an effective backup strategy.
- 85% of organizations store those backups in a remote facility to avoid physical disaster.
Backups should also be tested. Today, just over half of all organizations are periodically testing and validating backup data.
- Backups were periodically tested and validated in 59% of organizations assessed
In short, the security advantage comes from the fact that cloud providers have already implemented industry-leading security features that many organizations neglect to include in their local environments.
How does cloud cyber security differ from traditional cybersecurity?
The main difference between traditional security and cloud cyber security comes down to the shared responsibility model.
A traditional security program relies entirely on the organization in question allocating resources to securing their infrastructure. Due to this, the level of security is dependent on the investment the organization has made in its security staff and incident response preparedness, as well as other proactive measures like risk assessments, vulnerability scanning, penetration testing, and so on.
The shared responsibility model is exactly what it sounds like—the cloud service provider and the user of their product are both responsible for security, just different aspects of it. Broadly speaking, the service provider is responsible for their product, and the user/organization is responsible for how they access it.
What is the cloud service provider responsible for?
Cloud service providers (AWS, Google Workspace, Dropbox, Microsoft Azure, Salesforce CRM, etc.) are responsible for building and maintaining a secure product.
In addition to testing the software for vulnerabilities and releasing patches for any uncovered weaknesses quickly, cloud providers are also responsible for encrypting data transfer internally and externally so that sensitive files are not intercepted. These companies are also concerned with the uptime and reliability of their product, the physical security of their data centers and server rooms, and so on.
What is the user responsible for?
Despite their best efforts, no cloud provider can completely control how much effort a user puts into creating a secure password, storing it in a secure password manager, setting up MFA (though many are finally beginning to require the use of MFA), or making use of account recovery features.
Additionally, as with traditional security programs, organizations will always benefit from training their employees to look out for suspicious links and social engineering schemes. There are tools and services available to monitor inboxes and browser activity that lessen the burden associated with verifying the legitimacy of emails and reduce the likelihood of a staff member clicking on anything malicious in the first place.
While many of these practices are technically optional, it is a good idea to establish and enforce a security policy in your organization that invests in training for users and requires every staff member to follow certain guidelines as far as password protection, MFA, privileged access, and the sharing of sensitive information is concerned.
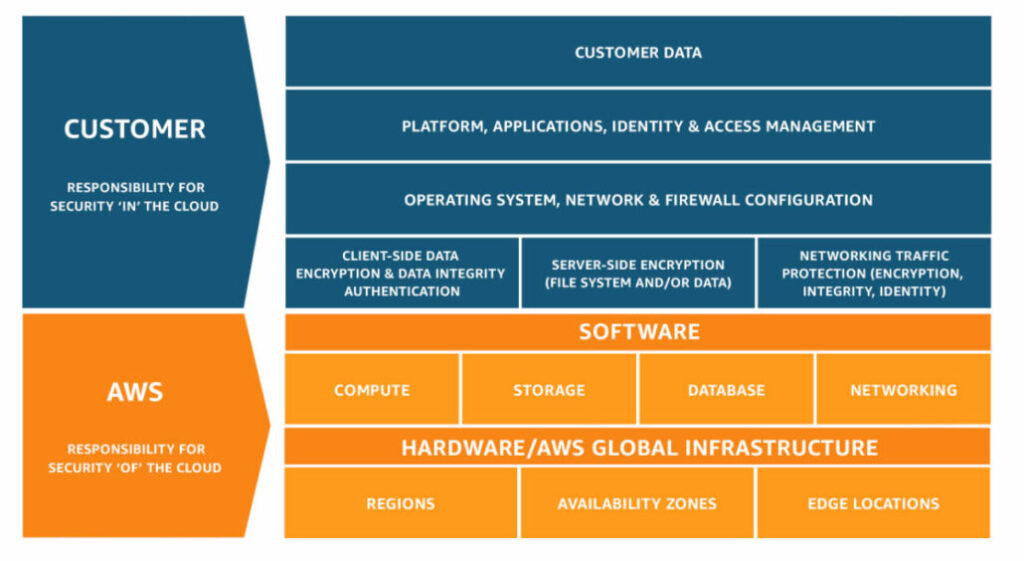
Here’s how AWS breaks down user/provider responsibilities
What are the cyber security Threats Associated with Cloud Computing?
Unfortunately, vulnerabilities in cloud infrastructure can exist. As long as staff members can access the contents of your cloud environment, there will be threat actors looking to swipe their credentials and gain access to your data—especially if security practices are lacking.
So what can potentially go wrong?
- Data Breaches – Unauthorized access to sensitive data due to misconfigurations or weak access controls.
- Insecure APIs – Vulnerabilities in Application Programming Interfaces (APIs) can be exploited for unauthorized access.
- Malware and Phishing Attacks – Traditional cyber threats persist in cloud environments, targeting users through malicious software and deceptive techniques.
- Data Loss – Accidental or intentional deletion of data without proper backups.
- Compliance Violations – Failure to meet regulatory requirements—this can even lead to legal consequences depending on the violation and type of compliance.
- Insufficient Identity and Access Management (IAM) – Weak controls over user access, opening the door to unauthorized usage.
Quick Tips: How to Securely Configure Your Cloud Environment
As you can see, it’s not that the threats are altogether different from what we’re used to seeing, but what’s more concerning is the lax security protocols we’ve observed in cloud environments due to organizations wrongly assuming that they are safer by nature.
As we discussed, cloud service providers are indeed responsible for providing security features for encryption, secure protocols, network architecture, and user access but you must still configure these!
A cloud environment can be secured effectively, but we cannot stress enough that you should not assume a cloud provider will configure security controls on your behalf and you should not fall into the trap of leaving everything set to the default settings.
- Encryption – While provided as an option, encryption is typically disabled by default. You must enable it.
- Secure Protocols – Cloud storage instances largely allow both HTTP and HTTPS requests for access by default. You must configure your cloud environment to deny HTTP requests.
- Network Architecture – By default, virtual networks typically have inbound and outbound subnet filtering set to ‘unrestricted’. Restrictions must be applied, otherwise, new instances created in that subnet will inherit the same default permissions.
- Multi-Factor Authentication – MFA is not always enabled by default. It too must be configured manually. This is one of the most important foundational practices in any security program and one that is still overlooked surprisingly often.
- Access Permissions – By default, all users will typically inherit permission policies. Policies should therefore be configured to be attached to groups, with users placed in groups with certain roles where access policies are inherited.
What’s the best way to avoid cloud security mistakes?
Organizations must realize they are ultimately responsible for securing their cloud footprint. This is, again, what the shared responsibility model is all about.
Despite the security features associated with a cloud environment, businesses must dedicate resources to managing security both initially and over time. Once internal resources are dedicated, they should take advantage of the many tools and external resources available to assist with security configurations.
- Lessen the burden on your staff to recognize threats. Utilize inbox filtering and other tools to reduce the likelihood of your users falling victim to a business email compromise.
- Employ least-privilege theory always. No one should have access to anything they don’t absolutely need access to.
- Training employees to recognize phishing and social engineering schemes is hugely beneficial as well. All the software, bells, whistles, and blinky lights in the world will do you no good if your staff hands over their password and MFA codes willingly.
- Follow best practices when configuring your environment. Don’t simply accept the default settings.
Thanks, as always, for reading!
